Several studies have determined that a large per cent of application security vulnerabilities could be prevented with improved security architecture, coding and pre-release security testing. We understand that our customers depend on our ability to build security into the development processes of design, coding and testing and assist them in becoming proactive in reducing the vulnerability threatscape. Our depth of experience and personnel enable Instinct Technique to uncover critical design and coding security exposures in complex software applications thereby reducing the overall risk exposure of the organization.
Instinct Technique's unique approach to application security is 100% process driven with the use of various automated software tools in addition to extensive manual testing by our security consultants.
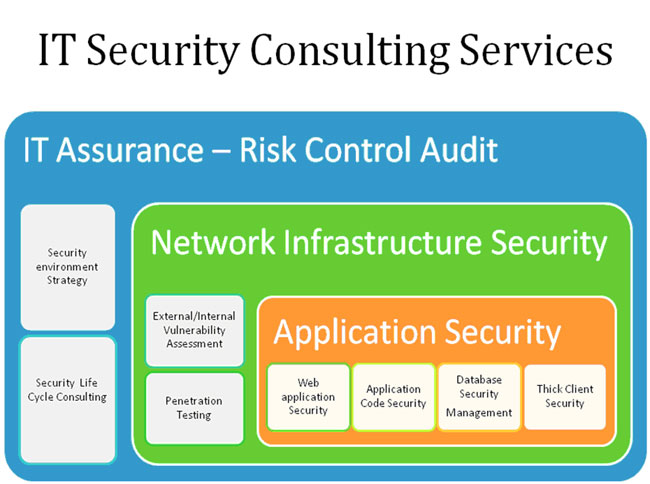
We conduct a multi-layer assessment to determine security requirements for each impacting domain such as the WAN/LAN, Web and Application servers, Database servers and other interfaces.
Instinct Technique Web application assessment involves, evaluating web applications for security vulnerabilities and provides proactive measurable recommendations. The assessment includes targeting the industry leading web application vulnerabilities.
Our approach includes extensive manual testing and verification in addition to automated web application assessment.
As a value addition to our clients our approach provides a thorough understanding of the customer's application architecture and business logic to ensure better results in identifying web vulnerabilities
Application Code review is the basic mechanism for validating the design and implementation of an application. It also helps maintain consistency in design and implementation practices across various applications within an enterprise. While an application assessment looks at an application from the outside in, the code review looks at an application from the inside out.
Instinct Technique's evaluation of the security configuration of a database identifies known weaknesses within the database account settings, server configurations, and SQL configuration that may allow unauthorized access to the data. Instinct Technique's Database security testing process includes:
Instinct Technique's approach to thick client assessments includes review of server side controls, data communication paths, and potential client related issues. Our process includes reviewing data communications between the server and client to identify communication or encryption vulnerabilities. In addition, our process includes review of files, registry, memory, and the actual application forms and sensitive information disclosures; Thick client assessment also includes bypass authentication controls of weak file, registry, memory, and network components or permissions.
Instinct Technique's Network Infrastructure Security is a complete 360 degree comprehensive approach to network security. The process covers all the key aspects of network-based assessments. The approach identifies all the common vulnerabilities as well as newly discovered ones. On a case-to-case basis we advise our clients to perform manual testing in addition to automated testing, to verify the findings and eliminate false positives.
Instinct Technique's IT Security consulting services includes evaluating the client's Internet and Intranet accessible network, systems, and applications for known security vulnerabilities.
The assessment provides a holistic view of the external and internal scans of the clients technology environments like vulnerabilities at the system, network, and application layer.
Penetration testing provides invaluable details to our clients in identifying and addressing the security issues that exist in clients' internal and external network environments. An effective penetration test simulates an attempt at breaching security so that the organization can better understand the risk factors involved and the potential consequences of an intrusion. The goal is to assess the infrastructure's security posture and attempt to exploit security flaws that might allow privilege escalation, disclosure of sensitive information, injection of malicious code into trusted components, invalid transactions, and other conditions generally recognized as posing security risks. We use industry proven testing methodologies some of which include voice, data, web based phishing and physical social engineering areas.
Instinct Technique's IT Risk Control Audit is designed to develop a clear understanding of your key controls like IT policies, IT processes, organization procedures, organizational structures and enterprise software and hardware in your environment. The objective of this review is to determine whether the IT Security Control practices are reasonable to support your technology infrastructure needs and are functioning as intended.
Instinct Technique offers security consulting as your strategic partner for your organization security strategy, policies, assessment, compliance, procedures to create a proactive security life cycle design to your enterprise.
2016 © Instinct Technique. ALL Rights Reserved.